I discovered thejavasea.me leaks AIO-TLP recently, and the experience was eye-opening. I am now more aware of how sensitive information can be compromised.
Thejavasea.me leaks AIO-TLP refers to a series of significant data breaches involving sensitive personal and organizational information. AIO-TLP stands for “All In One – Top Level Project,” indicating high-priority leaks.
In this article, we will delve into thejavasea.me leaks AIO-TLP, exploring their impact on personal and organizational data. We will examine what these leaks entail, their implications, and ways to protect yourself.
What Does Aio-Tlp Stand For?
AIO-TLP stands for “All In One – Top Level Project.” This term is used to describe a collection of highly important and sensitive information that has been leaked or exposed.

The “All In One” part means that the data is comprehensive and includes various types of information, while “Top Level” indicates that it’s of high priority or critical nature.
In the context of data leaks, AIO-TLP suggests that the leaked content is substantial and significant, often involving sensitive personal or corporate details. This makes the leaks particularly concerning because they can have serious implications for privacy and security.
Why Are Thejavasea.Me Leaks Significant?
Thejavasea.me leaks are significant because they often involve sensitive and private information that can severely impact individuals and organizations.
When personal data like names, addresses, or financial details are exposed, it can lead to identity theft, financial loss, and other security issues. This makes it crucial for affected parties to act quickly to protect themselves from potential harm.
Additionally, these leaks can damage the reputation of organizations involved. For businesses, leaked data can reveal confidential information or business secrets, affecting their credibility and trustworthiness.
The broader impact includes increased concerns about data security and privacy, making these leaks a serious issue in today’s digital world.
Read Also: The Ultimate Guide to the Cotopaxi Nido Bag 4 Litros
What Types Of Data Are Commonly Leaked?
- Personal Information: Names, addresses, phone numbers, and email addresses. This data can lead to identity theft and privacy violations.
- Financial Data: Bank account details, credit card numbers, and transaction records. Exposure of financial information can result in monetary losses and fraud.
- Corporate Secrets: Business plans, internal communications, and proprietary data. Leaked corporate information can damage a company’s reputation and competitive edge.
- Login Credentials: Usernames, passwords, and security questions. Compromised credentials can lead to unauthorized access to various accounts and systems.
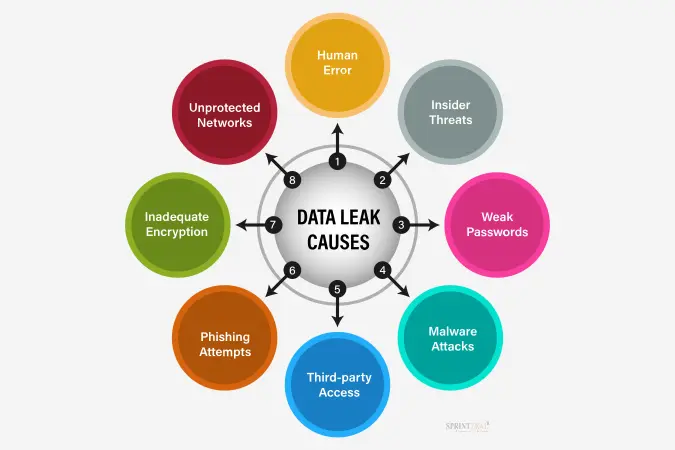
How Do Thejavasea.Me Leaks Occur?
Thejavasea.me leaks can occur through various methods. One common way is hacking, where cybercriminals break into databases or servers to steal sensitive information. These hackers often use advanced techniques to bypass security measures and access private data.
Another way leaks happen is through insider threats. This means that someone with access to the information, such as an employee or partner, might intentionally or accidentally expose it.
Additionally, poorly configured systems or security settings can leave data vulnerable to unauthorized access, leading to leaks.
Read Also: How to Start RandomGiantNet Blog? – A Comprehensive Guide
How Can Individuals Protect Themselves From Such Leaks?
Individuals can protect themselves from data leaks by using strong, unique passwords for their online accounts. It’s important to avoid using the same password across multiple sites and to create passwords that are hard to guess.

Additionally, enabling two-factor authentication adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, before accessing an account.
Staying informed about the latest security practices and being cautious with personal information online also helps protect against data leaks.
Regularly updating passwords and monitoring financial statements for any unusual activity can further safeguard your personal data and prevent potential damage from leaks.
What Role Do Authorities Play In Managing These Leaks?
Authorities play a crucial role in managing data leaks by investigating the incidents to identify and catch those responsible. They work with cybersecurity experts to trace the source of the leak and gather evidence. This helps prevent further damage and brings perpetrators to justice.
In addition to investigating, authorities also enforce regulations that require organizations to protect personal data and report breaches. They educate the public about online safety and best practices to help people protect their own information.
This combined effort is essential for reducing the impact of data leaks and improving overall cybersecurity.
Read Also: Comprehensive Guide to Disney Mirrorverse Mod APK Forum 13.0.0
Can You Provide Examples Of Notable Leaks?
Notable examples of data leaks include the Equifax data breach of 2017 and the Yahoo data breach of 2013-2014. The Equifax breach exposed the personal information of over 147 million people, including Social Security numbers and credit card details.

This massive leak highlighted how vulnerable sensitive financial information can be and the impact it can have on individuals’ financial security.
Another major leak was the Yahoo data breach, which affected all 3 billion of its user accounts. This breach compromised usernames, email addresses, and passwords, making it one of the largest leaks in history.
Both incidents underscore the importance of robust security measures to protect personal and corporate data from being exposed.
What Are Future Trends In Data Security?
Future trends in data security include the use of artificial intelligence (AI) to enhance protection measures. AI can analyze vast amounts of data to identify potential threats and detect unusual activities more quickly than traditional methods.
This helps in preventing breaches before they occur and responding faster if a security issue arises.
Another trend is the adoption of blockchain technology, which provides a secure way to record transactions and store data. Blockchain’s decentralized nature makes it harder for hackers to alter information, offering an extra layer of protection.
Additionally, stricter regulations are expected to be implemented to ensure better data protection and hold organizations accountable for safeguarding personal information.
Conclusion:
Thejavasea.me leaks AIO-TLP involve a series of major data breaches that reveal sensitive personal and organizational information. AIO-TLP, which stands for “All In One – Top Level Project,” signifies that these leaks are of high importance and priority.
Read Also:
- Appfordown Appstore – The Smart Way To Find And Download Apps!
- 1660.26/2: A Comprehensive Guide
- Understanding the Importance of the DRZ400 Piston Rod Retainer
FAQs:
Why are these leaks a big concern?
They pose risks to privacy, security, and can lead to financial and reputational damage.
What can individuals do to protect themselves?
Using strong passwords, enabling two-factor authentication, and staying updated on security practices are key steps.
What role do authorities play in these situations?
Authorities investigate the leaks, enforce regulations, and help educate the public on protecting their data.